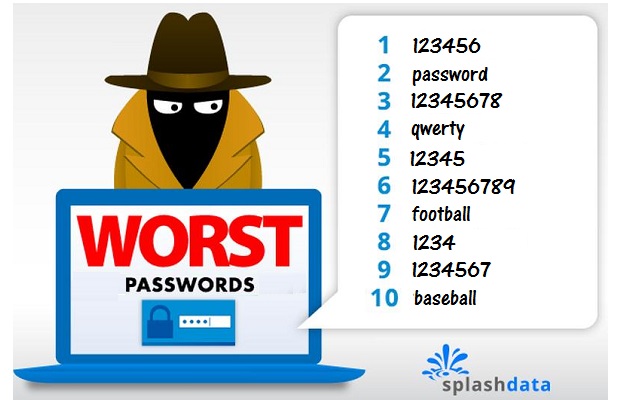
The 25 worst passwords of 2015 have been released by SplashData, indicating that many people are still failing to protect themselves online.
The company, which makes password management software, compiles the annual list from the most common passwords leaked online each year — more than two million in 2015.
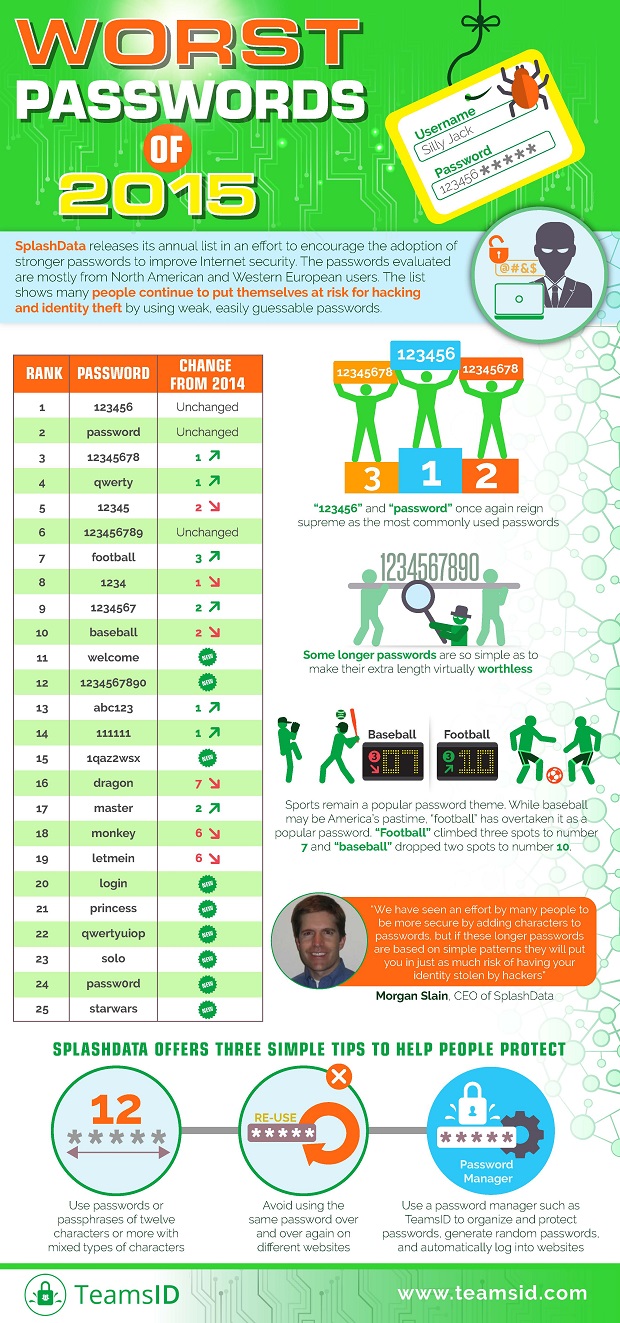
The password 123456 and “password” itself remain the top two commonly used passwords, respectively – as they have every year since SplashData started compiling the annual list in 2011.
“Baseball” and “football” both made the top 10, as usual, but football (#7, up from #10) overtook baseball (#10, down from #8) in popularity.
Three new popular passwords on the list may be blamed, in part, on this year’s release of Star Wars: The Force Awakens: starwars, solo and princess.
The top password recalls this famous scene from the movie Spaceballs:
View the top 20 list here or full infographic below:
Analysis
As the report proves that a huge number of web users are leaving their accounts and data exposed to exploitation and fraud, three top IT security professionals give their view of how to avoid a security disaster.
Gavin Millard, Technical Director EMEA at Tenable Network Security:
“Irrelevant of what usual suspects make up the top 25, the fact that a list is still compilable in 2016 is a reflection on the apathetic approach many users take to securing their information online. Individual passwords should either be created using a recipe per site, an automated tool like a password manager or by using a suggested password by the browser.
“To reduce the risk of data loss, organisations need to enforce password best practices (length, strength, complexity), educate users on the importance of credential management, and roll out two factor authentication where applicable to ensure employees can’t use poor passwords on corporate resources.”
Matt Marx, Information Security Consultant at MWR InfoSecurity:
“With the number of high profile data breaches on the rise, users and organisations alike are more concerned than ever before with securing their sensitive data. One of the simplest means of acquiring this information for an attacker is to enter an organisation with the key to the door itself, users’ passwords.
“Authentication is the process of proving that you are who you say you are. There are a number of digital methods that we can use to prove that someone is indeed who they claim to be. The most common means of doing this is to provide a secret piece of information, such as a password. This secret bit of information is intended to be something that only the user knows or has access to. However, users often land up choosing information that is not secret to them, and also common among other users.
“The list of the most common passwords from 2015 is no surprise. We see year in and year out the same kinds of passwords being chosen by users to safeguard their accounts. As an information security company, MWR has performed extensive research around cracking passwords. In addition to using common passwords, such as can be seen in the top 25 password list compiled by SplashData, MWR’s research has shown that attackers can target the personal lives of users in order to improve their chances of guessing their password. This includes the kind of language that they use to post on social media, the organisation they work for and the kinds of websites they frequent. These factors can give an attacker an idea about the kind of password a user is likely to choose and target an attack against that user using this information. MWR demonstrated the effectiveness of this type of attack with a proof-of-concept tool called WordHound released in 2014. In order to crack users’ passwords, researchers and attackers alike use powerful GPU password cracking rigs. The rig that MWR uses can perform over 20 billion guesses a second against Microsoft Windows password hashes. In fact, a user that had a password in the top 25 passwords would have their password guessed by such a rig in under a second.”
Richard Cassidy, Technical Director – EMEA, at Alert Logic:
“Given all the recent and historical news on data breaches of personal e-mail accounts, social media accounts and even phone account passwords, it is every wonder therefore that we are still using password combinations that are incredibly easy to guess. The challenge is Cyber Criminals are well aware that many of their targets still fail to employ a strong password policy and as such will “pre-load” their dictionary attacks for brute-force access with the combinations listed; which in turn means almost instant access to a substantial number of users personal data. Passwords such as these are dangerous because they are the first attempted combinations in the arsenal of attackers brute-force access tools.
Unfortunately however, even with complex passwords we are almost fighting a loosing battle; this is because cyber criminals can access botnet ecosystems to crack encrypted files or password protected data (through hashes of the password, or direct brute force attack) or make use of underground “cracking rigs” that use GPU’s Processors in rigs that can quite literally attempt billions of combinations per second. This means your average 8 character password (mandated by many online systems today) can be cracked in days. A great deal of research has gone into the minimum password length recommended; all users should be choosing passwords of at least 12 characters (alphanumeric with special characters) that are completely random and that would challenge even the most sophisticated decryption rigs for service out there on the cyber criminal underground.
Overall there are two approaches to protecting your data; first is access to data stores (e-mail, social media, online file sharing) with a minimum of 12 character passwords and second, encrypted key data files with strong cipher algorithms. In the end, you want to make the cost of accessing that data far outweigh the value of it, or at least provide a level of assurance that by the time it could be theoretically accessed, it is no longer useful to the source that exfiltrated it. However even if you fail to do any of this, don’t make cyber criminals job any easier by choosing easy password phrases.”
Andy Green, Technical Specialist at Varonis:
“People are bad at coming up with their own passwords. We’re all guilty! For convenience, we make them obvious or short or both. Hackers are good and getting better all the time at breaking them, either though brute force guessing or dictionary-style attacks if the hackers have access to the password hash. Keep in mind that a password with only six characters can be one of around 200 billion combinations – not a large number in the current era of big data. By increasing your password by only two characters, you’ve increased the possible combinations to almost a quadrillion – which will result in a serious computation challenge for attacker. Sure, you should have at least 8 characters, but better yet use the ‘correct horse battery staple’ method. What’s that? Essentially, it’s a memory trick where each letter of the password represents a word in a story. So ’I just wrote a comment about passwords for the press’ becomes ‘Ijwacapftp’. That’s an unguessable password for hackers but one that you’ll never forget!”