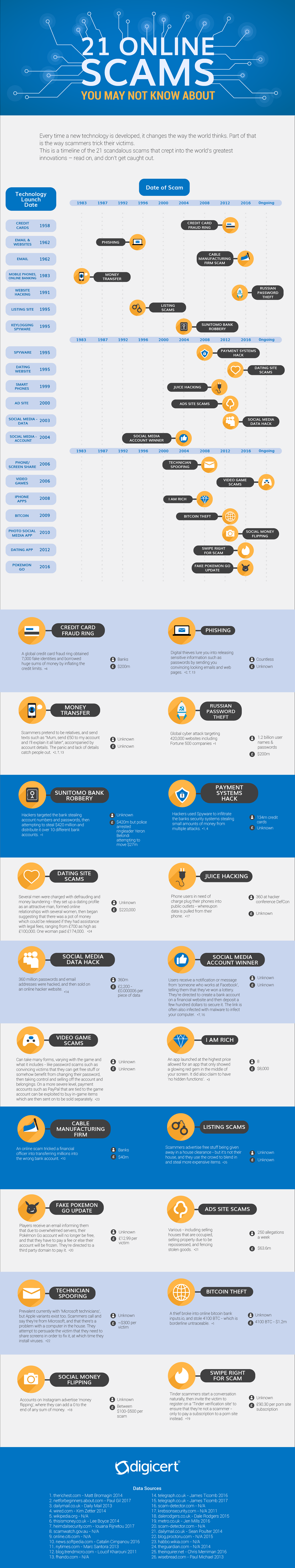
From credit cards to dating sites, this infographic shows how digital data has been used and abused over time.
DigiCert‘s latest research analyses the evolution of digital crime and uncovers how technology can be used to defraud both individuals and companies.
Ultimately, it is hoped that these findings will aid tech users in becoming more vigilant against potential crime.
Some of the key findings were that:
• Individuals are most likely to be targeted in their leisure time. This is particularly true of dating-site scams.
• Cryptocurrency is set to be the new frontier, and there is already a surprising history of Bitcoin heists.
• Gamers are particularly at risk of online crime, where one of the biggest names compromised is Pokemon Go!
With recent questions over the security of online personal data, many people are becoming wary of how their online presence can endanger their finances, and even their mental and emotional health.
Across all areas of digital technology, crime is evolving. Rapidly-changing technology forces scammers to change their tactics regularly. But can the public keep up? Internet security provider DigiCert have highlighted some of the most shocking tactics scammers can use – which now puts consumers one step ahead of the game.
Digital crime: a new phenomenon?
Online crime might feel like a modern phenomenon, however this research indicates that individuals and businesses alike have been targeted via technology for decades, in increasingly creative and crafty ways.
• Fraudulent Money Transfers – One of the earliest crimes to emerge was that of fraudulent money transfers via mobile phone in the 1980s. Since then, scams have become more sophisticated.
• Social Money Flipping – Recent social media criticisms have been based around personal data, but this Ponzi-style scam from earlier in the decade took up to $100-500 per victim
• Swipe Right for Scam – Even the relatively modern invention of the dating app has been subject to cyber-attacks, with phishing ‘verification’ requests robbing people by tricking them into paying a subscription to another site.
• Technician Spoofing – Online trickery has been targeting people less internet-savvy people by posing as Microsoft or Apple employees, and then installing viruses on their computers.
Many of these scams target people in their leisure time, when they’re more likely to be caught off-guard:
• This is especially true of dating-site scams, where people are arguably more vulnerable, putting their hearts on the line and placing trust in strangers. The after-effects can be both financially and emotionally devastating, with one woman losing nearly £200,000 to a man she thought would be a new love.
• Cryptocurrency is set to be the new frontier of crime, with one of the first major heists taking place in 2009. With the value of Bitcoin soaring and a chronic lack of regulation, the next attack is likely just around the corner, and will have a much greater impact on people’s financial situation across the globe.
• Gamers are particularly at risk of online crime, with an untold number of victims having had millions stolen from them over the years. Scams targeting gamers range from password and sensitive data theft, to PayPal accounts being hacked and used to make multiple payments. One of the most prevalent and high-profile recent schemes is the fake Pokemon Go update, taking £12.99 from each of its many victims.
You can find the timeline here to trace all game-changing scams, from the credit card scam from the 1980s, to the Russian Password scam from only a few years ago.
Methodology
The infographic breaks down each individual scam, indicating the year the technology was developed, the date of the cornerstone scams, as well as detailing the financial gain and method of each scam. Analysing the tactics of previous crimes is a sure-fire way to remain alert and discerning in a world where constant vigilance is required online.
Indeed, the recent controversies surrounding the likes of Facebook have shown us that the landscape of personal data exploitation is rapidly changing, which our research intrinsically reflects.
Source: https://www.digicert.com/